If you are searching about Remote Sensing | Free Full-Text | Good Practices for Object-Based you've visit to the right page. We have 9 Pics about Remote Sensing | Free Full-Text | Good Practices for Object-Based like Sensors | Free Full-Text | Detection-Response Task—Uses and Limitations, Sensors | Free Full-Text | HelpResponder—System for the Security of and also Sensors | Free Full-Text | Detection-Response Task—Uses and Limitations. Here it is:
Remote Sensing | Free Full-Text | Good Practices For Object-Based
Sensors | Free Full-Text | Detection-Response Task—Uses And Limitations
 www.mdpi.com
www.mdpi.com
Sensors | Free Full-Text | VaryBlock: A Novel Approach For Object
 www.mdpi.com
www.mdpi.com
(PDF) Threats Of Password Pattern Leakage Using Smartwatch Motion
 www.researchgate.net
www.researchgate.net
recognition sensors leakage smartwatch threats password motion pattern using
Sensors | Free Full-Text | HelpResponder—System For The Security Of
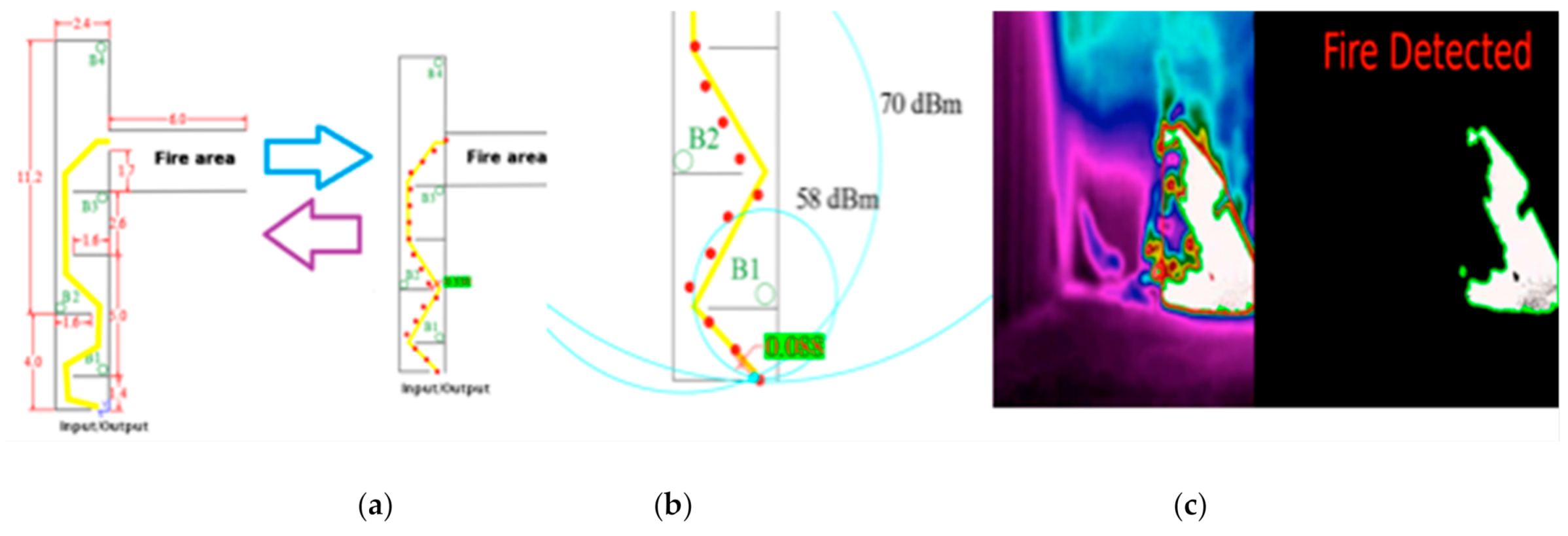 www.mdpi.com
www.mdpi.com
Object Tracking Using The Proximity Sensor From V-REP - YouTube
 www.youtube.com
www.youtube.com
Sensors | Free Full-Text | VaryBlock: A Novel Approach For Object
 www.mdpi.com
www.mdpi.com
Sensors | Special Issue : Sensors For Object Detection, Classification
 www.mdpi.com
www.mdpi.com
Sensors | Free Full-Text | Detection-Response Task—Uses And Limitations
detection limitations task response uses figure sensors
(pdf) threats of password pattern leakage using smartwatch motion. Detection limitations task response uses figure sensors. Recognition sensors leakage smartwatch threats password motion pattern using
0 comments
Post a Comment